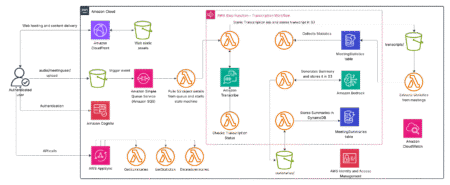
Extracting meaningful insights from unstructured data presents significant challenges for many organizations. Meeting recordings, customer interactions, and interviews contain invaluable…
Development
Aligned representations across languages is a desired property in multilingual large language models (mLLMs), as alignment can improve performance in…
The ever-increasing parameter counts of deep learning models necessitate effective compression techniques for deployment on resource-constrained devices. This paper explores…
Latest PEAR Releases: Text_LanguageDetect 1.0.2 Text_LanguageDetect 1.0.1 Archive_Tar 1.6.0 Source: Read MoreÂ
#744 — July 11, 2025 Read on the Web JavaScript Weekly Vercel Acquires NuxtLabs — Vercel has acquired the company…
The blog discusses how AI is leveling up the QA outsourcing industry by enhancing efficiency, improving code quality, and reducing costs. You will learn how to choose the right AI-driven QA partner and see how intelligent testing strategies can help you stay competitive in the digital age.
The post Lead with Intelligence: Rethink QA Outsourcing for the AI Age first appeared on TestingXperts.
CVE ID : CVE-2025-7913
Published : July 21, 2025, 12:15 a.m. | 23 hours, 59 minutes ago
Description : A vulnerability, which was classified as critical, was found in TOTOLINK T6 4.1.5cu.748_B20211015. Affected is the function updateWifiInfo of the component MQTT Service. The manipulation of the argument serverIp leads to buffer overflow. It is possible to launch the attack remotely. The exploit has been disclosed to the public and may be used.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7914
Published : July 21, 2025, 1:15 a.m. | 22 hours, 59 minutes ago
Description : A vulnerability has been found in Tenda AC6 15.03.06.50 and classified as critical. Affected by this vulnerability is the function setparentcontrolinfo of the component httpd. The manipulation leads to buffer overflow. The attack can be launched remotely.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7916
Published : July 21, 2025, 6:15 a.m. | 17 hours, 59 minutes ago
Description : WinMatrix3 developed by Simopro Technology has an Insecure Deserialization vulnerability, allowing unauthenticated remote attackers to execute arbitrary code on the server by sending maliciously crafted serialized contents.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7918
Published : July 21, 2025, 6:15 a.m. | 17 hours, 59 minutes ago
Description : WinMatrix3 Web package developed by Simopro Technology has a SQL Injection vulnerability, allowing unauthenticated remote attackers to inject arbitrary SQL commands to read, modify, and delete database contents.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7343
Published : July 21, 2025, 7:15 a.m. | 16 hours, 59 minutes ago
Description : The SFT developed by Digiwin has a SQL Injection vulnerability, allowing unauthenticated remote attackers to inject arbitrary SQL commands to read, modify, and delete database contents.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7344
Published : July 21, 2025, 7:15 a.m. | 16 hours, 59 minutes ago
Description : The EAI developed by Digiwin has a Privilege Escalation vulnerability, allowing remote attackers with regular privileges to elevate their privileges to administrator level via a specific API.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7921
Published : July 21, 2025, 7:15 a.m. | 16 hours, 59 minutes ago
Description : Certain modem models developed by Askey has a Stack-based Buffer Overflow vulnerability, allowing unauthenticated remote attackers to control the program’s execution flow and potentially execute arbitrary code.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2024-6107
Published : July 21, 2025, 9:15 a.m. | 14 hours, 59 minutes ago
Description : Due to insufficient verification, an attacker could use a malicious client to bypass authentication checks and run RPC commands in a region. This has been addressed in MAAS and updated in the corresponding snaps.
Severity: 9.6 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-50151
Published : July 21, 2025, 10:15 a.m. | 13 hours, 59 minutes ago
Description : File access paths in configuration files uploaded by users with administrator access are not validated.
This issue affects Apache Jena version up to 5.4.0.
Users are recommended to upgrade to version 5.5.0, which does not allow arbitrary configuration upload.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2024-13974
Published : July 21, 2025, 2:15 p.m. | 9 hours, 59 minutes ago
Description : A business logic vulnerability in the Up2Date component of Sophos Firewall older than version 21.0 MR1 (20.0.1) can lead to attackers controlling the firewall’s DNS environment to achieve remote code execution.
Severity: 8.1 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7382
Published : July 21, 2025, 2:15 p.m. | 9 hours, 59 minutes ago
Description : A command injection vulnerability in WebAdmin of Sophos Firewall versions older than 21.0 MR2 (21.0.2) can lead to adjacent attackers achieving pre-auth code execution on High Availability (HA) auxiliary devices, if OTP authentication for the admin user is enabled.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7624
Published : July 21, 2025, 2:15 p.m. | 9 hours, 59 minutes ago
Description : An SQL injection vulnerability in the legacy (transparent) SMTP proxy of Sophos Firewall versions older than 21.0 MR2 (21.0.2) can lead to remote code execution, if a quarantining policy is active for Email and SFOS was upgraded from a version older than 21.0 GA.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6704
Published : July 21, 2025, 2:15 p.m. | 9 hours, 59 minutes ago
Description : An arbitrary file writing vulnerability in the Secure PDF eXchange (SPX) feature of Sophos Firewall versions older than 21.0 MR2 (21.0.2) can lead to pre-auth remote code execution, if a specific configuration of SPX is enabled in combination with the firewall running in High Availability (HA) mode.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-46116
Published : July 21, 2025, 3:15 p.m. | 8 hours, 59 minutes ago
Description : An issue was discovered in CommScope Ruckus Unleashed prior to 200.15.6.212.14 and 200.17.7.0.139, and in Ruckus ZoneDirector prior to 10.5.1.0.279, where an authenticated attacker can disable the passphrase requirement for a hidden CLI command `!v54!` via a management API call and then invoke it to escape the restricted shell and obtain a root shell on the controller.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…