Cybersecurity researchers have detailed four different vulnerabilities in a core component of the Windows task scheduling service that could be…
Security
Cheap Android smartphones manufactured by Chinese companies have been observed pre-installed with trojanized apps masquerading as WhatsApp and Telegram that…
By Associate Professor Dr. Sheeba Armoogum, University of Mauritius In 2025, the paradigms of human hacking are undergoing a substantial…
A data breach at insurance firm Lemonade left the details of thousands of drivers’ licenses exposed for 17 months. According…
Intro: Why hack in when you can log in? SaaS applications are the backbone of modern organizations, powering productivity and…
On April 14, 2025, 4Chan, the infamous anonymous image board, experienced downtime due to unexplained outages that left users frustrated…
Cybersecurity researchers have unearthed a new controller component associated with a known backdoor called BPFDoor as part of cyber attacks…
North Korean hackers sent more than 120,000 phishing emails to nearly 18,000 individuals over a three-month campaign that impersonated South…
Introduction Cyber threats targeting supply chains have become a growing concern for businesses across industries. As companies continue to expand…
Threat actors are leveraging an artificial intelligence (AI) powered presentation platform named Gamma in phishing attacks to direct unsuspecting users…
Google on Wednesday revealed that it suspended over 39.2 million advertiser accounts in 2024, with a majority of them identified…
The U.S. government funding for non-profit research giant MITRE to operate and maintain its Common Vulnerabilities and Exposures (CVE) program…
Academic institutions have a unique set of characteristics that makes them attractive to bad actors. What’s the right antidote to…
Cybersecurity researchers have disclosed a malicious package uploaded to the Python Package Index (PyPI) repository that’s designed to reroute trading…
A critical security vulnerability has been disclosed in the Apache Roller open-source, Java-based blogging server software that could allow malicious…
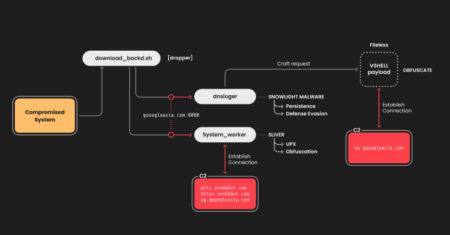
The China-linked threat actor known as UNC5174 has been attributed to a new campaign that leverages a variant of a…
In episode 46 of The AI Fix, China trolls US tariffs, a microscopic pogoing flea-bot makes a tiny leap forward…
RansomHouse is a cybercrime operation that follows a Ransomware-as-a-Service (RaaS) business model, where affiliates (who do not require technical skills…
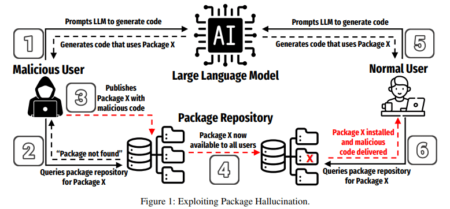
Code-generating large language models (LLMs) have introduced a new security issue into software development: Code package hallucinations. Package hallucinations occur…
Cyble researchers have uncovered ransomware called DOGE BIG BALLS, a ransomware that not just stands out but also presents its…