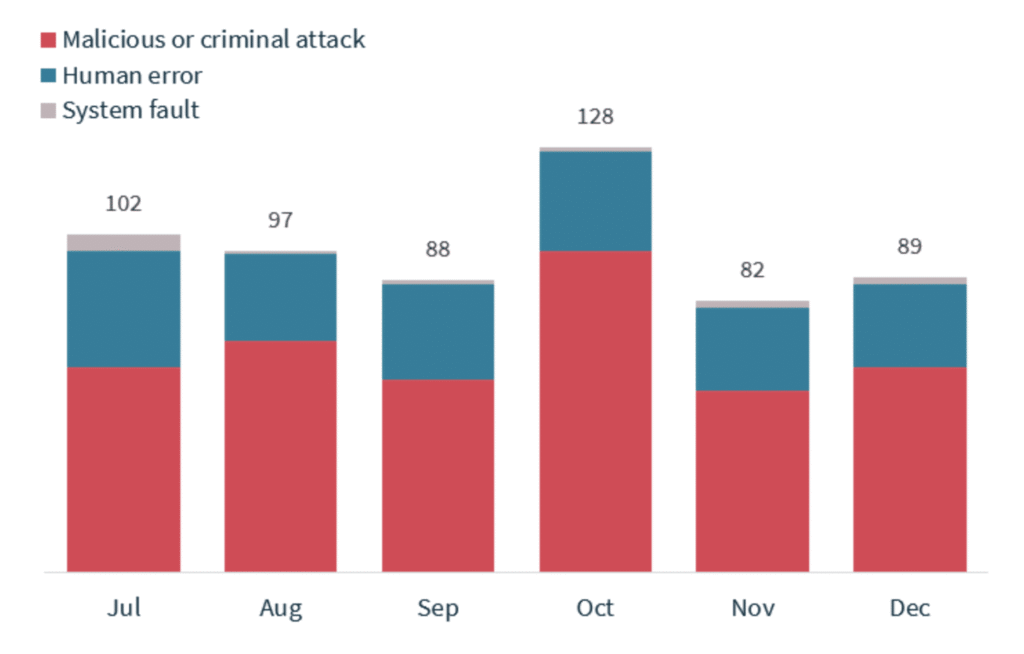
Australia is facing a troubling uptick in data breaches, with the country recording its highest number of reported incidents this decade. According to the Office of the Australian Information Commissioner (OAIC), 527 data breaches notifications occurred between July and December 2024—up 9% from the first half of the year, and the highest tally since late 2020.
The findings, published in OAIC’s latest Notifiable Data Breaches (NDB) report, highlight deepening fault lines in the country’s cybersecurity defenses—especially within health, finance, government, and supply chains.
Ransomware, Phishing, and Australia’s Credential Crisis
Malicious or criminal attacks drove most of the reported breaches, accounting for 67% of incidents. Within that category, cyber incidents made up two-thirds. Ransomware attacks rose sharply—up 24%—and OAIC analysts say phishing and stolen credentials continue to lead the charge in initial access methods.
In fact, compromised credentials were the root cause in a quarter of all breaches. That stat should alarm anyone still running without multi-factor authentication or relying on static passwords in enterprise environments.
Health and Government in the Crosshairs
Sector-wise, health took the lion’s share of breaches with 102 notifications, followed closely by government entities at 63. Financial institutions reported 58, education clocked in at 44, and the retail sector disclosed 29 breaches.

Why the health sector? It’s a high-value target. Patient records are rich with identity data and difficult to replace, making them prime commodities on dark web marketplaces. Government agencies, meanwhile, are often targeted by both cybercriminals and nation-state actors seeking political leverage.
The Supply Chain is the New Battleground
One of the biggest shifts in the report is the rise in “multi-party breaches.” The OAIC received 121 secondary notifications—cases where a breach in one organization rippled out to affect multiple entities. In most instances, the root cause was a third-party service provider.
In other words: you’re only as strong as your weakest vendor.
That finding echoes global breach trends, where attacks on IT service providers, cloud platforms, and managed security vendors become launchpads for mass compromise. It also underscores why vendor risk assessments and tighter contractual controls are no longer optional.
Human Error Still Abounds
Despite all the headlines around ransomware, human error continues to be a stubborn threat. Thirty percent of breaches were caused by employee mistakes—from sending data to the wrong recipient to failing to use BCC in mass emails. Another 3% were tied to system faults, such as misconfigured databases or software glitches.

The takeaway: the human layer is still one of the weakest links in the cybersecurity chain, and organizations ignoring user awareness and data handling protocols do so at their peril.
Delays, Disclosure, and Ticking Clocks
Perhaps the most concerning revelation? Delay in disclosure. A full 26% of organizations took more than 30 days to notify OAIC after identifying a breach. That lag time can be the difference between users taking protective action—or suffering the full brunt of identity theft and fraud.

OAIC Commissioner Angelene Falk didn’t mince words and said prompt notification is key to minimizing harm. Organizations need to have mature breach detection and response processes that kick in the moment an incident is detected.
Also read: Australia’s New Cyber Security Act: Mandatory Ransom Payment Reporting
What Comes Next?
The OAIC’s recommendations echo the usual cybersecurity hygiene checklist: implement multi-factor authentication, train staff regularly, and ensure data breach response plans are tested and ready. But the subtext is clear—organizations can’t treat privacy as a box-ticking exercise. As the regulatory spotlight sharpens, the cost of inaction will grow.
Australia’s privacy laws are also on a collision course with modernization. Reforms to the Privacy Act 1988 are currently under review, with proposals to expand the OAIC’s enforcement powers and increase penalties for non-compliance. If passed, Australia could be looking at a future where data protection is enforced not just through shame but with real legal and financial consequences.
Australia’s latest data breach figures should be a wake-up call—not just for CISOs, but for CEOs, boards, and vendors in every sector. The adversaries are getting smarter. The risks are multiplying. And as the OAIC report makes clear, the era of casual compliance is over.
Source: Read More