Versa Networks has patched three vulnerabilities in its Concerto network security and SD-WAN orchestration platform, including one that scored a 10.0, the highest possible severity rating.
The Versa Concerto vulnerabilities were revealed by Project Discovery in a blog post earlier this week, which said Versa hadn’t responded to the researchers’ disclosures that were first made in February. The researchers said they had “not received any response or indication of a forthcoming patch. As a result, we are compelled to publish our findings to raise awareness and prompt the necessary actions to secure affected systems.”
However, in a statement to The Cyber Express, Versa said the vulnerabilities were fixed with a hotfix on March 7 and then in the Concerto 12.2.1 general release on April 16. Versa offered a screenshot as proof of the April 16 fix. Versa also said the company had been in touch with the researchers.
“There is no indication that these vulnerabilities were exploited in the wild, and no customer impact has been reported,” Versa said. “All affected customers were notified through established security and support channels with guidance on how to apply the recommended updates.”
The Versa Concerto Vulnerabilities
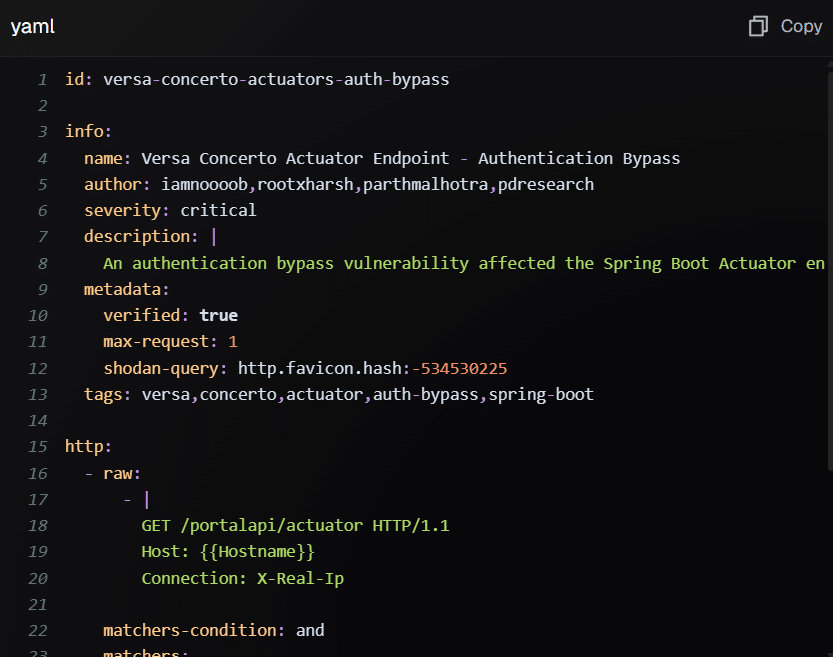
The Versa Concerto vulnerabilities have been assigned the following CVEs:
- CVE-2025-34027, a 10.0-rated Race Condition and Improper Authentication vulnerability. The Versa Concerto platform in versions 12.1.2 through 12.2.0 is vulnerable to an authentication bypass in the Traefik reverse proxy configuration, which could allow an attacker to access administrative endpoints. The Spack upload endpoint can potentially be leveraged with a Time-of-Check to Time-of-Use (TOCTOU) write in combination with a race condition to achieve remote code execution via path loading manipulation.
- CVE-2025-34026, a 9.2-severity Improper Authentication vulnerability. The authentication bypass in the Traefik reverse proxy configuration could potentially allow the internal Actuator endpoint to be leveraged for access to heap dumps and trace logs.
- CVE-2025-34025, an 8.6-severity Incorrect Permission Assignment for Critical Resource vulnerability. The Concerto platform is vulnerable to a privilege escalation and container escape vulnerability caused by unsafe default mounting of host binary paths that allow the container to modify host paths. The escape could potentially be used to trigger remote code execution or direct host access, depending on host operating system configuration.
“These vulnerabilities, when chained together, could allow an attacker to fully compromise both the application and the underlying host system,” the Project Discovery researchers wrote. “This research highlights how small misconfigurations in modern cloud-based deployments can escalate into severe security risks, particularly for platforms handling sensitive network configurations and enterprise data.”
Versa’s Response
With a customer base that includes enterprises and service providers, a Versa vulnerability can have significant effects, so the company’s prompt response was the right one.
“Versa follows responsible disclosure practices and takes a proactive approach to identifying, mitigating, and communicating potential risks,” the company told The Cyber Express. “Security is foundational to our platform, and we continue to invest in continuous monitoring, rapid response, and customer education as part of our commitment to trust and protection.”
Many customers have already upgraded to the April 16 release, the company said, “though we recognize some deployments may still be pending.”
Detailed information on affected releases and mitigation steps is limited to customer access only, Versa said.
Source: Read More