During penetration testing many times we need to register on websites and they send a lots of mails. Even sometime we don’t want to share our original e-mail id. Then how we can hide ourself from website’s eye?
git clone github.com/kavishgr/tempomail
cd tempomail
go build .
Now we need to move this tempomail file to /usr/local/bin where the software installed locally by using following command:
sudo mv tempomail /usr/local/bin/
Now we have installed tempomail successfully. We can check it via running following command from anywhere in terminal:
tempomail -h
Here in the following screenshot we can see that our emails will locally saved on /tmp/1secmails/ by default. We can change it by using -path string.
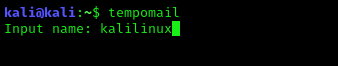
Now we can set our custom mail by using tempomail. To do this we run tempomail command in our terminal:
tempomail
After this we got a mail id with this name. Shown in the following screenshot:
Now if anyone send mails on this email id we got the mail. Yoo, We got an e-mail. After we got a mail in our inbox it shows like following:
To open our mailbox we need to open another terminal window and type following command:
ls /tmp/1secmails/
The above command shows a mail in the directory.
Now we can see what’s inside the mail using cat (or any text viewer or editor tool). We run the following command to see the mail.
This is how we can receive an e-mail on our custom temporary mail id running on command line. We found this good at bypass the e-mail verification during penetration testing and avoid spam or unwanted mails on our original mail id.
This is how we can create our custom disposable e-mail address directly from our terminal.
Love our articles? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxInfamily, join our Telegram Group & Whatsapp Channel. We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.
Source: Read More