This blog is offered to readers who may be interested in seeing how Apple Pay fits into their payment priorities. Whether executives of merchants or financial intuitions, Apple Pay is an ultra-secure global payment platform too large to ignore. I noted recently while paying for my morning coffee and donut (shh, don’t tell the wife) from a sidewalk cart in Manhattan that the cart accepted Apple Pay, Zelle, Venmo, and Google Pay. Upon inquiring, the cart owner explained that none of the students from the nearby college ever had cash but always had their phones. In addition to helping my barista, this blog will be of value to executives focused on modernizing the payment experience and provides advantages of both Apple Pay and similar digital wallet platforms versus traditional credit card usage.
Apple Pay is a digital wallet, similar to Google Pay, Samsung Pay, et. al. that allows users to store (tokenize) and use payment methods. With an estimated 638 million Apple Pay users worldwide as of yearend 2024, the volume of payments is huge. In 2022, Apple Pay processed $6 Trillion in digital payments.
Tokenization
Tokenization, similar to how for decades New York City’s transit system allowed and even required users to substitute their money for tokens that could be used on the city’s subways and buses, is the process of replacing a card’s 16-digit number on their plastic card with a unique alternate card number. That unique alternate card number, which is an algorithmically generated number, is the token and is unique to each card, user, and device and can be used for purchases.
Unlike the physical tokens used by NYC subways, a digital token holds no value. If it falls into the hands of a hacker, it’s useless since they cannot reverse it back to the 16-digit number Primary Account Number (“PAN”) on the physical plastic card.
The graphic below shows the 7 steps required for the first time a particular credit card is entered into an Apple Wallet in a particular device:
GRAPHIC 1:
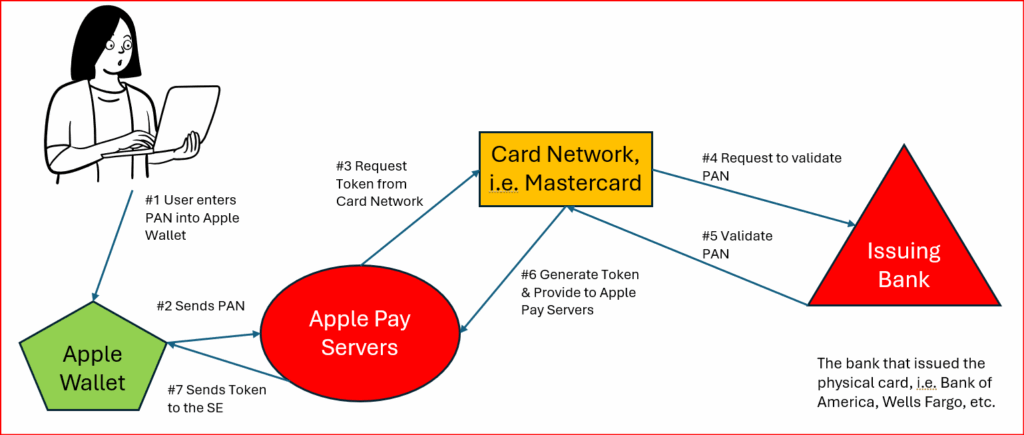
Why Apple Pay is So Secure
When the user adds their credit card to their wallet application for Apple Pay use (step 1), it’s assigned a token, which in Apple talk is referred to a Device Account Number (“DAN”). The DAN is specific to an Apple device. If you add your card to another device, it will have a new DAN. This is critical for identity security and fraud protection.
To ensure maximum security, iPhones and computers utilize a dedicated Secure Element (“SE”) chip to store encrypted payment tokens. These tokens represent your credit card information but are unreadable by unauthorized parties.
The advantages of tokens are similar to the advantages of tokens that were used by the New York City Transit system. They don’t contain any personal information, just as the real-life tokens did not, and speed payment, just as a real-life token allowed users to board the bus faster rather than the driver counting their nickels to ensure the full fare had been paid. Apple Pay tokens keep changing, which makes it the most secure method to complete payments.
Users can pay via Near Field Communications (“NFC”) in-person, or Online. NFC is a short-range wireless technology that allows two electronic devices to communicate when placed within 3 inches of each other. Apple has provided NFC in iPhones since the iPhone 6, and the Apple Watch since inception.
Advantages of Apple Pay (or Tokenized payment platform) vs a regular credit card
- Apple Pay utilizes a dynamic security code instead of the standard four-digit security code on credit or debit cards.
- Apple Pay generates a security code for each transaction, preventing anyone from stealing your card details to make unauthorized purchases.
- If you lose your Apple device when Apple Pay is activated, you can stop all transactions using the Find My iPhone service. Additionally, users can activate lost mode on your iPhone. Even if their iPhone is stolen, the thief still requires your passcode, Touch ID, or Face ID to authorize purchases.
- The merchant never sees your data. Additionally, Apple doesn’t store your credit or debit card numbers on the device or its servers.
GRAPHIC 2:
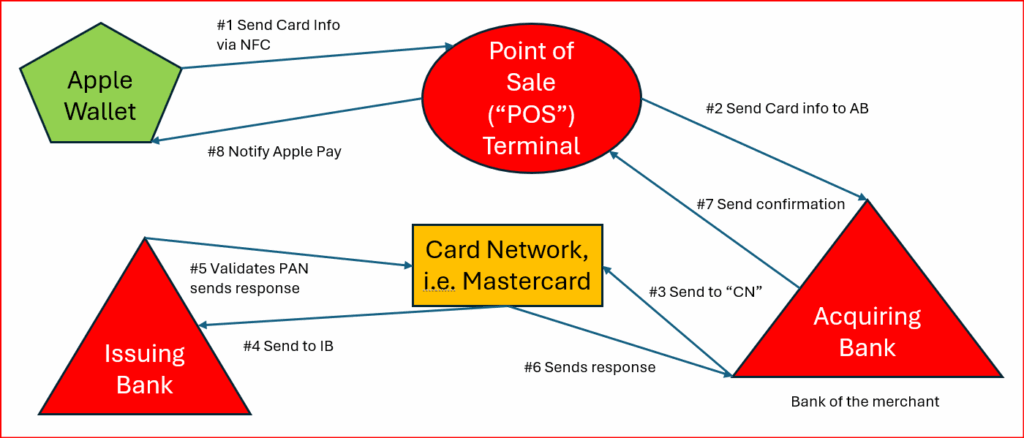
Usage of Apple Pay by Country
The following table shows that despite my teenage daughter’s best efforts, the United States’ share of Apple Pay penetration is not yet the largest in the world in either physical or online purchases, suggesting that Apple Pay’s explosive growth is likely to continue.
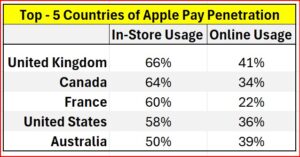
The above table uses statistics publicly available from Capital One Shopping
Ready to explore your firm’s payments strategy?
Our financial services experts continuously monitor the regulatory landscape and deliver pragmatic, scalable solutions that meet the mandate and more. Reach out to Perficient’s Financial Services Managing Director David Weisel to discover why we’ve been trusted by 18 of the top 20 banks, 16 of the 20 largest wealth and asset management firms, and are regularly recognized by leading analyst firms.
Source: Read MoreÂ



