In today’s cloud-first world, securing your DNS layer is more critical than ever. DNS (Domain Name System) is a foundational element of network infrastructure, but it’s often overlooked as a security risk. Attackers frequently exploit DNS to launch phishing campaigns, exfiltrate data, and communicate with command-and-control servers. Proactive DNS security is no longer optional – it’s essential.
To strengthen DNS-layer security, Amazon Route 53 Resolver DNS Firewall provides robust control over DNS traffic by enabling the use of domain lists, allowing specific domains to be explicitly permitted or denied. Complementing these custom lists are AWS Managed Domain Lists, which autonomously block access to domains identified as malicious, leveraging threat intelligence curated by AWS and its trusted security partners. While this method is highly effective in countering known threats, cyber adversaries are increasingly employing sophisticated evasion techniques that go undetected by conventional blocklists. In this blog, I’ll explore DNS vulnerabilities, introduce Route 53 Resolver DNS Firewall, and walk you through practical strategies to safeguard your cloud resources.
By analyzing attributes such as query entropy, length, and frequency, the service can detect and intercept potentially harmful DNS traffic, even when interacting with previously unknown domains. This proactive approach enhances defense against advanced tactics, such as DNS tunneling and domain generation algorithms (DGAs), which attackers often use to establish covert communication channels or maintain malware connectivity with command-and-control servers.
In this blog, I’ll guide you through a hands-on journey into the world of DNS-layer threats and the tools available to defend against them. You’ll discover how to configure effective Route 53 Resolver DNS Firewall Advanced rules. I’ll also walk through a real-world threat detection scenario, demonstrating how the service seamlessly integrates with AWS Security Hub to provide enhanced visibility and actionable alerts. By the end of this post, you’ll be equipped with the knowledge to implement DNS Firewall rules that deliver intelligent, proactive protection for your AWS workloads.
Risks Linked to DNS Tunneling and Domain Generation Algorithms
DNS tunneling and Domain Generation Algorithms (DGAs) are sophisticated techniques employed by cyber adversaries to establish hidden communication channels and evade traditional security measures.
DNS Tunneling: This method exploits the DNS protocol by encapsulating non-DNS data within DNS queries and responses. Since DNS traffic is typically permitted through firewalls and security devices to facilitate normal internet operations, attackers leverage this trust to transmit malicious payloads or exfiltrate sensitive data without detection. The risks associated with DNS tunneling are significant, including unauthorized data transfer, persistent command-and-control (C2) communication, and the potential for malware to bypass network restrictions. Detecting such activity requires vigilant monitoring for anomalies such as unusually large DNS payloads, high-frequency queries to unfamiliar domains, and irregular query patterns.
Domain Generation Algorithms (DGAs): DGAs enable malware to generate a vast number of pseudo-random domain names, which are used to establish connections with Command and Control (C2) servers. This dynamic approach makes it challenging for defenders to block malicious domains using traditional blacklisting techniques, as the malware can swiftly switch to new domains if previous ones are taken down. The primary risks posed by DGAs include the resilience of malware infrastructures, difficulty in predicting and blocking malicious domains, and the potential for widespread distribution of malware updates. Effective mitigation strategies involve implementing advanced threat intelligence, machine learning models to detect anomalous domain patterns, and proactive domain monitoring to identify and block suspicious activities.
Understanding and addressing the threats posed by DNS tunneling and DGAs are crucial for maintaining robust cybersecurity defenses.
Let’s See How DNS Firewall Works
Route 53 Resolver DNS Firewall Advanced enhances DNS-layer security by intelligently analyzing DNS queries in real time to detect and block threats that traditional firewalls or static domain blocklists might miss. Here’s a breakdown of how it operates:
-
Deep DNS Query Inspection
When a DNS query is made from resources within your VPC, it is routed through the Amazon Route 53 Resolver. DNS Firewall Advanced inspects each query before it is resolved. It doesn’t just match the domain name against a list—it analyses the structure, behaviour, and characteristics of the domain itself.
-
Behavioural Analysis Using Machine Learning
The advanced firewall uses machine learning models trained on massive datasets of real-world domain traffic. These models understand what “normal” DNS behaviour looks like and can flag anomalies such as:
- Randomized or algorithm-generated domain names (used by DGAs)
- Unusual query patterns
- High entropy in domain names
- Excessive subdomain nesting (common in DNS tunnelling)
This allows it to detect suspicious domains, even if they’ve never been seen before.
-
Confidence Thresholds
Each suspicious query is scored based on how closely it resembles malicious behaviour. You can configure confidence levels—High, Medium, or Low:
- High Confidence: Detects obvious threats, with minimal false positives (ideal for production).
- Medium Confidence: Balanced sensitivity for broader detection.
- Low Confidence: Aggressive detection for highly secure or test environments
-
Action Controls (Block, Alert, Allow)
Based on your configured rules and confidence thresholds, the firewall can:
- Block the DNS query
- Alert (log the suspicious activity, but allow the query)
- Allow known safe queries
These controls give you flexibility to tailor the firewall’s behavior to your organization’s risk tolerance.
-
Rule Groups and Customization
You can organize rules into rule groups, apply AWS Managed Domain Lists, and define custom rules based on your environment’s needs. You can also associate these rule groups with specific VPCs, ensuring DNS protection is applied at the network boundary.
-
Real-Time Response Without Latency
Despite performing deep inspections, the firewall processes each DNS request in under a millisecond. This ensures there is no perceptible impact on application performance.
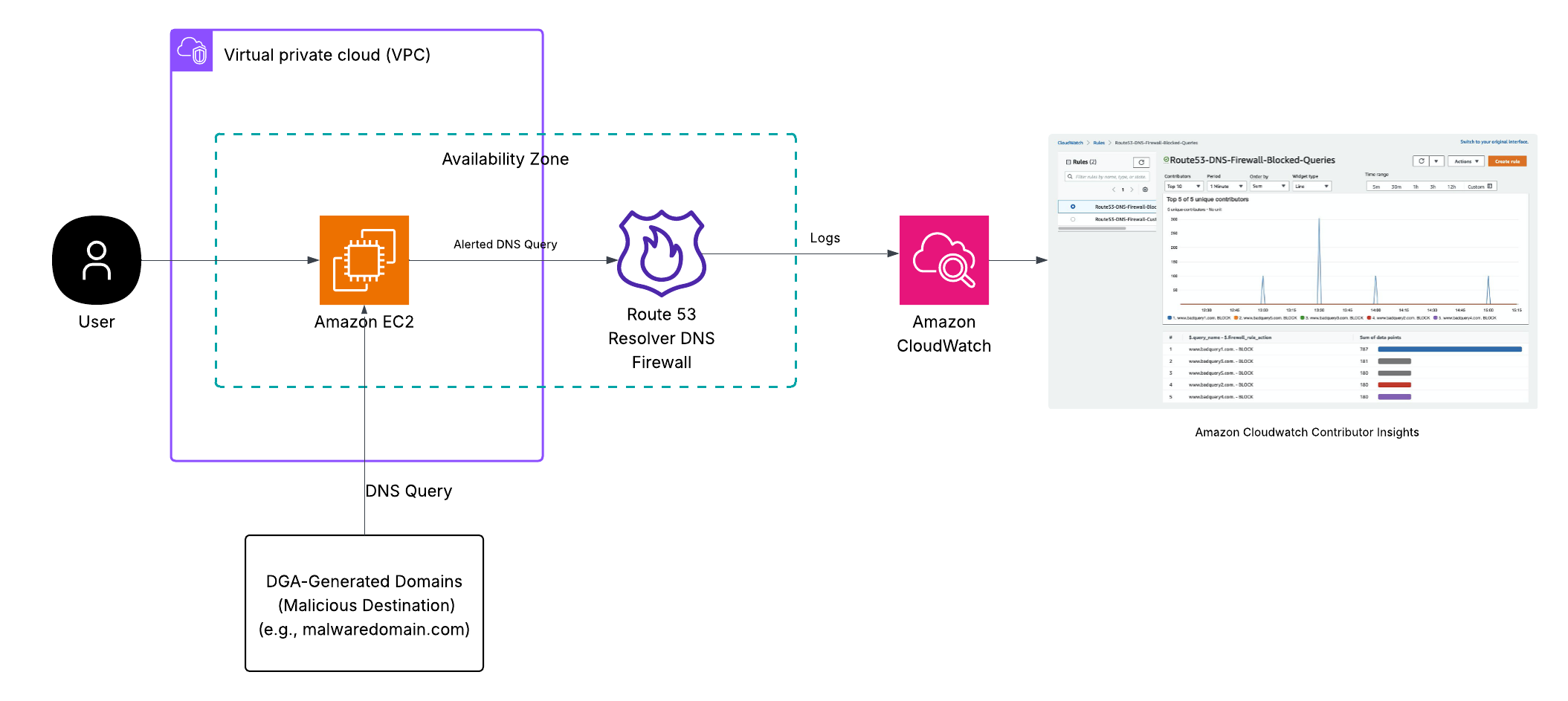
The above figure shows Route 53 DNS Firewall logs ingested into CloudWatch and analysed through Contributor Insights.
Demonstration
To begin, I’ll demonstrate how to manually create a Route 53 Resolver DNS Firewall Advanced rule using the AWS Management Console. This rule will be configured to block DNS queries identified as high-confidence DNS tunneling attempts.
Step 1: Navigate to Route 53 Resolver DNS Firewall
- Sign in to the AWS Management Console.
- In the search bar, type “Route 53” and select “Route 53 Resolver”.
- In the left navigation pane, choose “DNS Firewall Rule groups” under the DNS Firewall section.

Step 2: Create a New Rule Group
- Click on “Create rule group”.
- Enter a name and optional description (e.g., BlockHighConfidenceDNS
- Click Next to proceed to add rules.
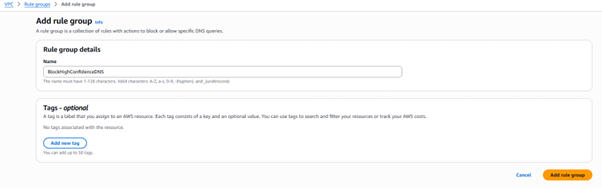
Step 3: Add a Rule to the Rule Group
- Click “Add rule”.

- For Rule name, enter a name (e.g., BlockTunnelingHighConfidence).
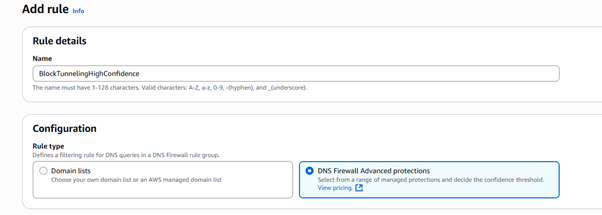
- Under DNS Firewall, Advanced protection
- Select DNS tunneling detection.
- For the Confidence threshold, select High.
- Leave the Query Type field blank to apply the rule to all query types.
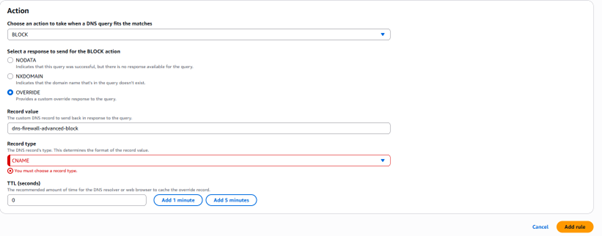
- Under the Action Section:
- Set the Action to Block.
- For the Response type, choose OVERRIDE.
- In the Record value field, enter: dns-firewall-advanced-block.
- For the Record type, select CNAME.
- Click Add rule to save the configuration.
Monitoring and Insights
Route 53 Resolver query logging offers comprehensive visibility into DNS queries originating from resources within your VPCs, allowing you to monitor and analyze DNS traffic for both security and compliance purposes. When enabled, query logging captures key details for each DNS request—such as the queried domain name, record type, response code, and the source VPC or instance. This capability becomes especially powerful when paired with Route 53 Resolver DNS Firewall, as it enables you to track blocked DNS queries and refine your security rules based on real traffic behavior within your environment. Below are sample log entries generated when the DNS Firewall identifies and acts upon suspicious activity, showcasing the depth of information available for threat analysis and incident response.
Example log entry: DNS tunneling block
The following is an example of a DNS tunneling block.
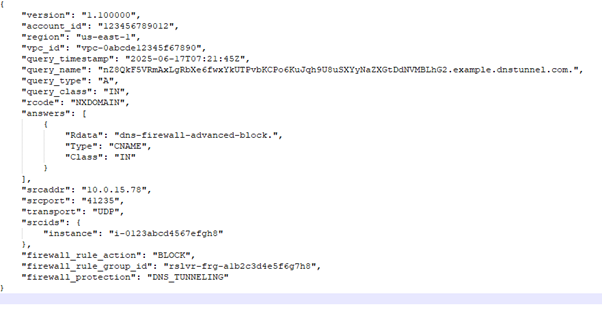
Key Indicators of DNS Tunneling
- query_name: Very long, random-looking domain name—typical of data being exfiltrated via DNS.
- rcode: NXDOMAIN indicates no valid domain exists—often seen in tunneling.
- answers: The query response was overridden with a controlled CNAME (dns-firewall-advanced-block.).
- firewall_rule_action: Shows this was an intentional BLOCK action.
- firewall_protection: Labeled as DNS_TUNNELING, indicating why the query was blocked.
- srcids: Helps trace back to the source EC2 instance making the suspicious request.
Example log entry: DNS tunneling alert
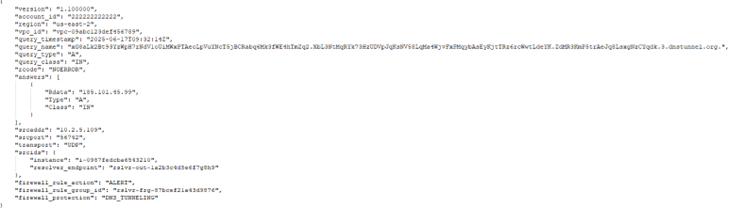
Use Case
This type of alert is useful in:
- Monitoring mode during firewall tuning.
- Staging environments where you want visibility without enforcement.
- Incident investigations—tracking which resources may be compromised or leaking data.
Final Thoughts
Amazon Route 53 Resolver DNS Firewall Advanced marks a significant advancement in protecting organizations against sophisticated DNS-layer threats. As discussed, DNS queries directed to the Route 53 Resolver take a distinct route that bypasses conventional AWS security measures such as security groups, network ACLs, and even AWS Network Firewall, introducing a potential security blind spot within many environments. In this post, I’ve examined how attackers exploit this gap using techniques like DNS tunneling and domain generation algorithms (DGAs), and how Route 53 Resolver DNS Firewall Advanced leverages real-time pattern recognition and anomaly detection to mitigate these risks. You also explored how to set up the service via the AWS Management Console and deploy it using a CloudFormation template that includes pre-configured rules to block high-confidence threats and alert on suspicious activity. Additionally, you saw how enabling query logging enhances visibility into DNS behavior and how integrating with AWS Security Hub consolidates threat insights across your environment. By adopting these capabilities, you can better safeguard your infrastructure from advanced DNS-based attacks that traditional blocklists often miss, strengthening your cloud security posture without compromising performance.
Source: Read MoreÂ



