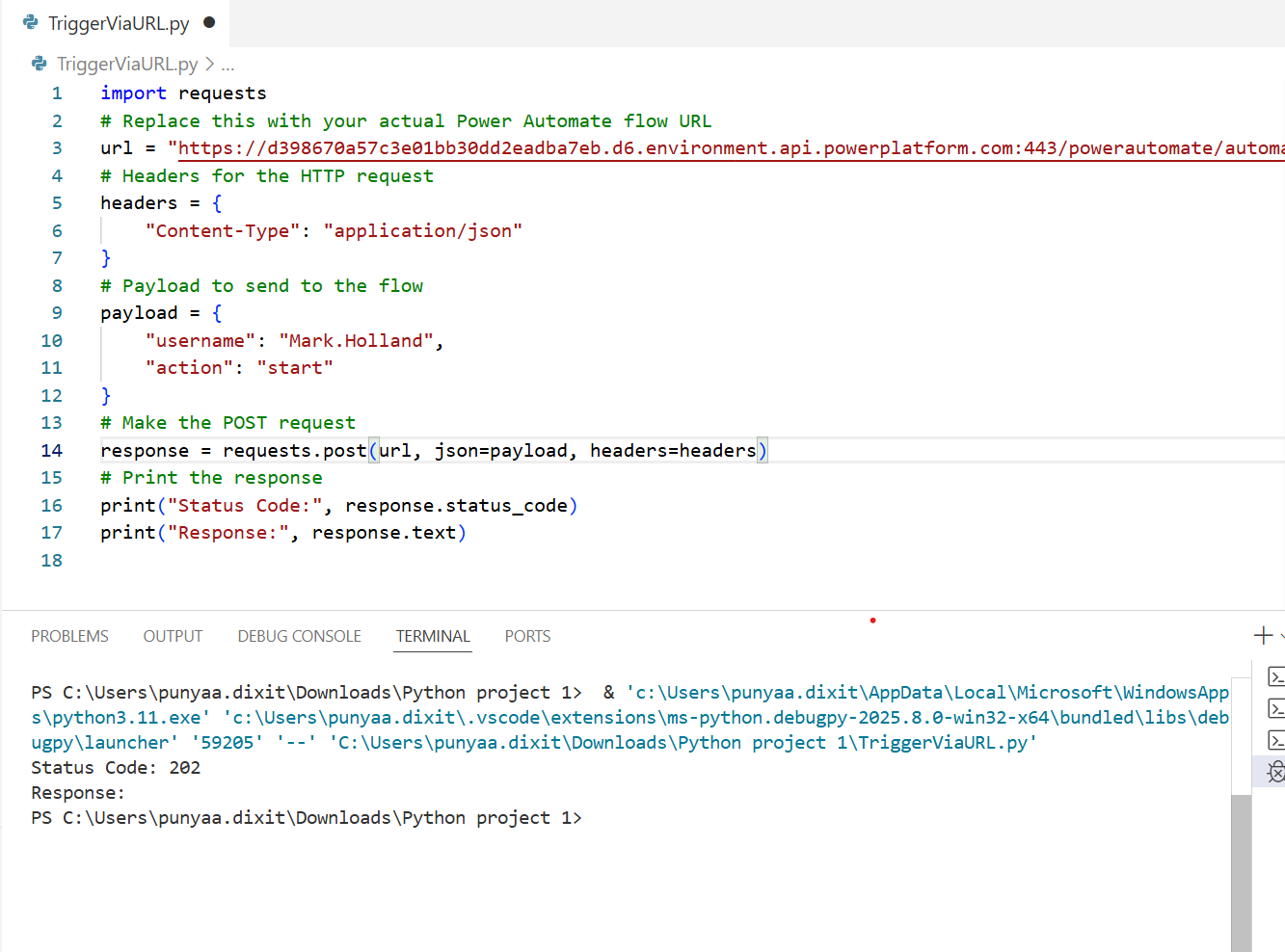
Want to trigger Power Automate flows from anywhere using just a URL—even from a Python script? Whether you’re working with automation scripts, web apps, or external systems, Power Automate makes it easy to integrate workflows using HTTP requests. In this guide, you’ll learn how to set up a flow that can be triggered via URL—step by step—with real-world examples, including how to do it using Python.
This is what your final flow would look like: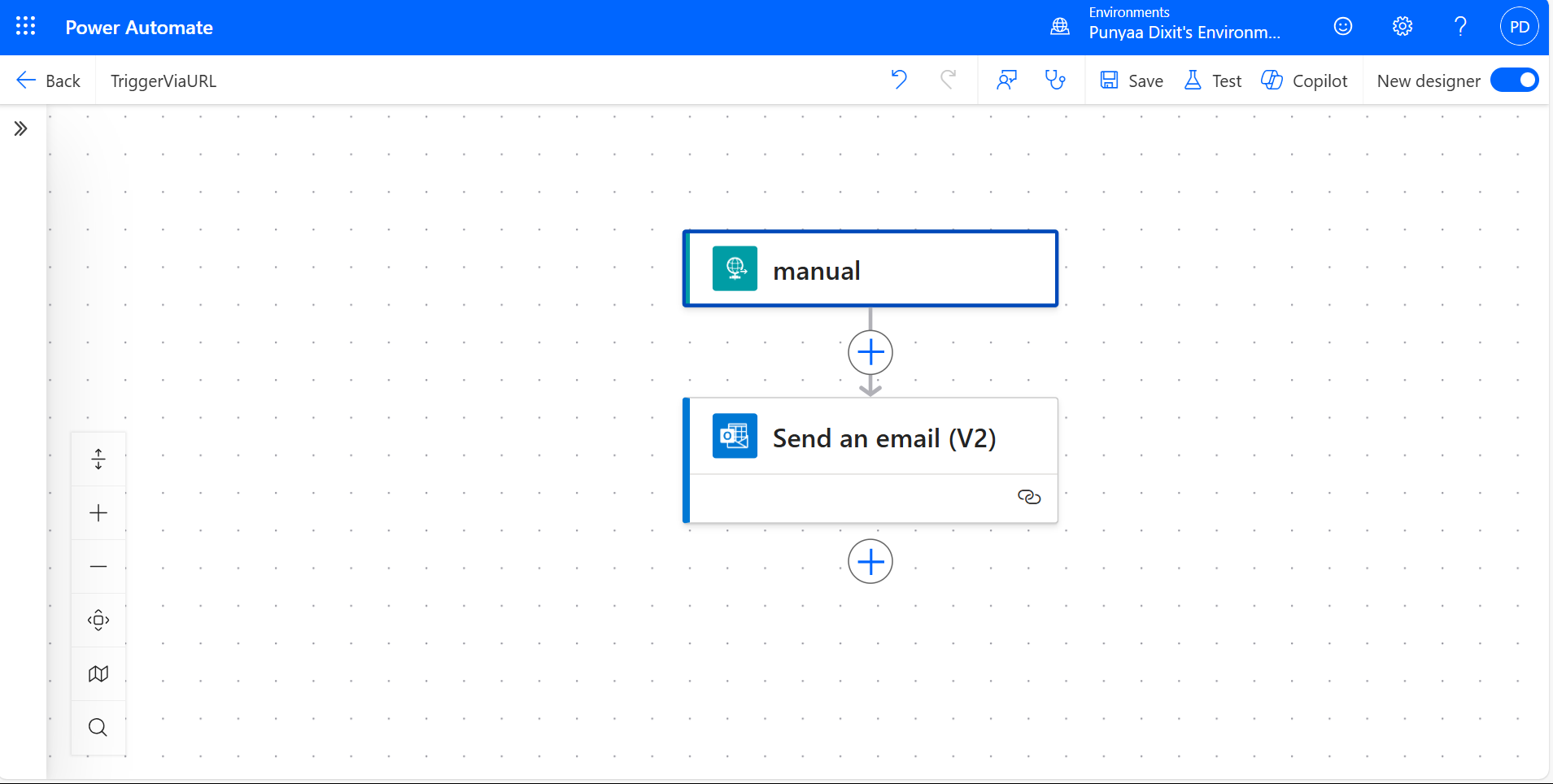
Step 1: Create a Flow to Trigger Power Automate via URL
- Go to Power Automate (https://make.powerautomate.com)
- Click Create > Instant cloud flow.
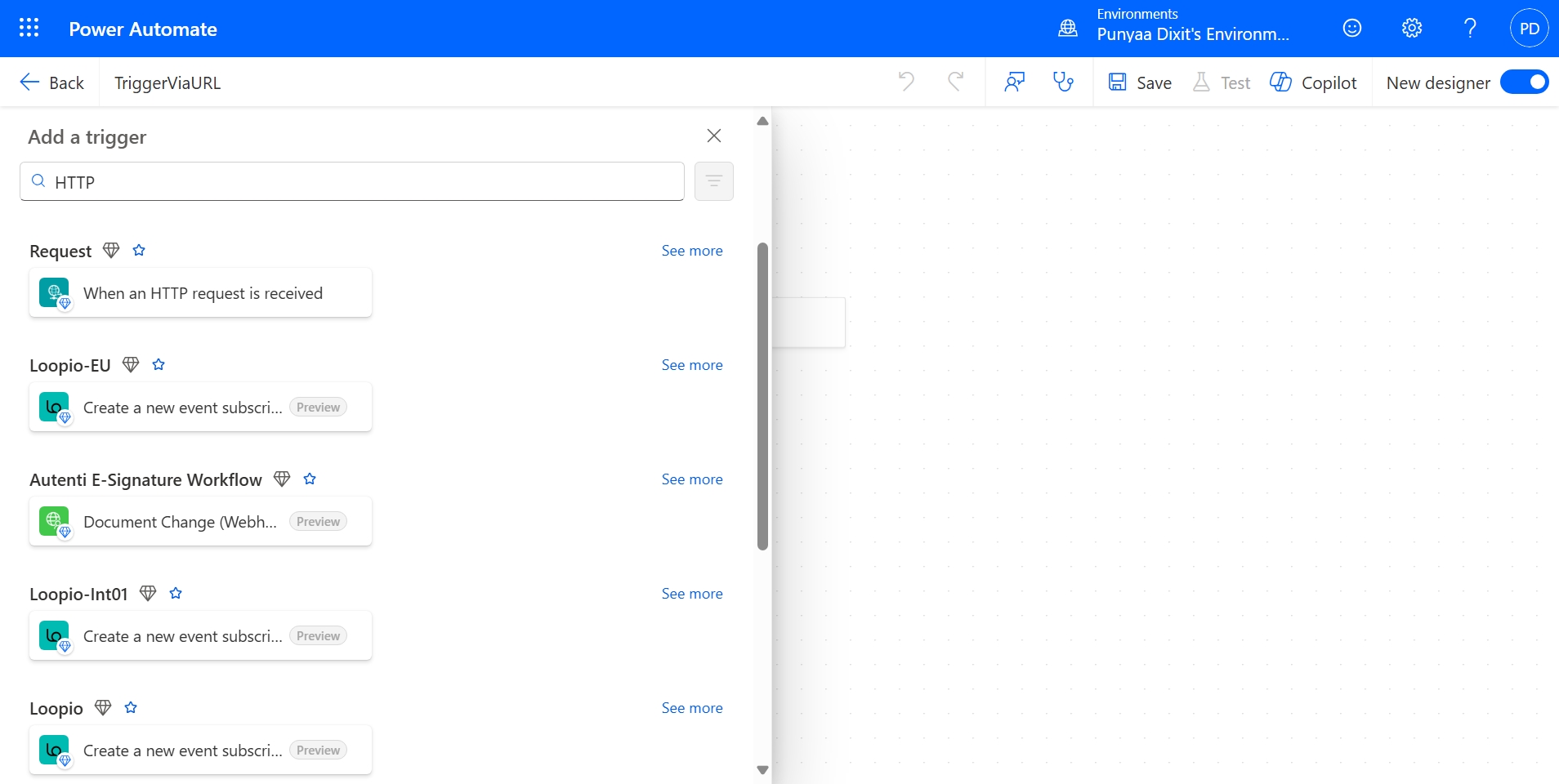
- Choose “When an HTTP request is received” as the trigger.
- Name your flow (e.g., TriggerViaURL) and click Create.
Step 2: Define the JSON Schema
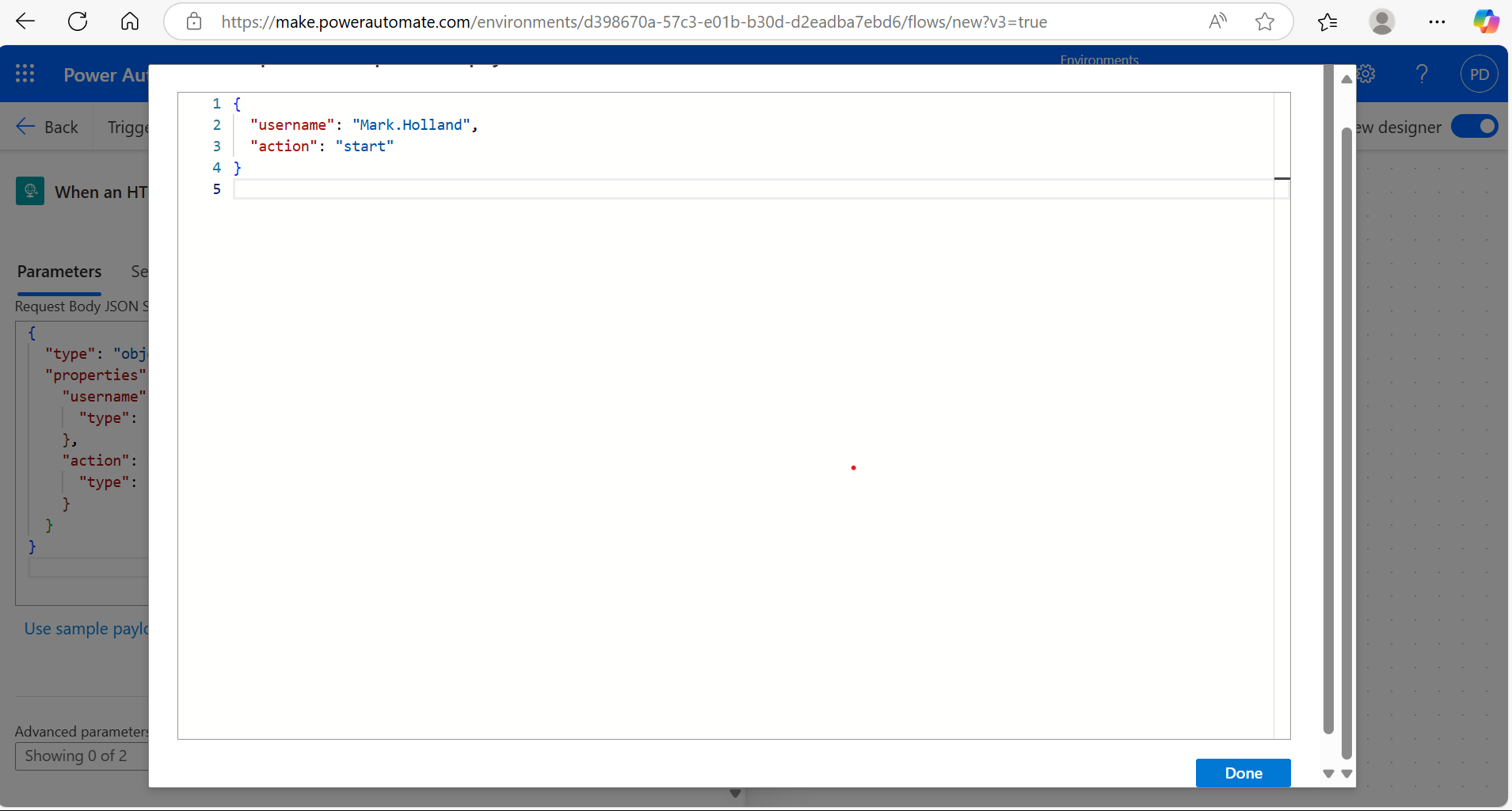
If you want to pass data in the request, click on the trigger and define your required Parameters and JSON schema. For example: 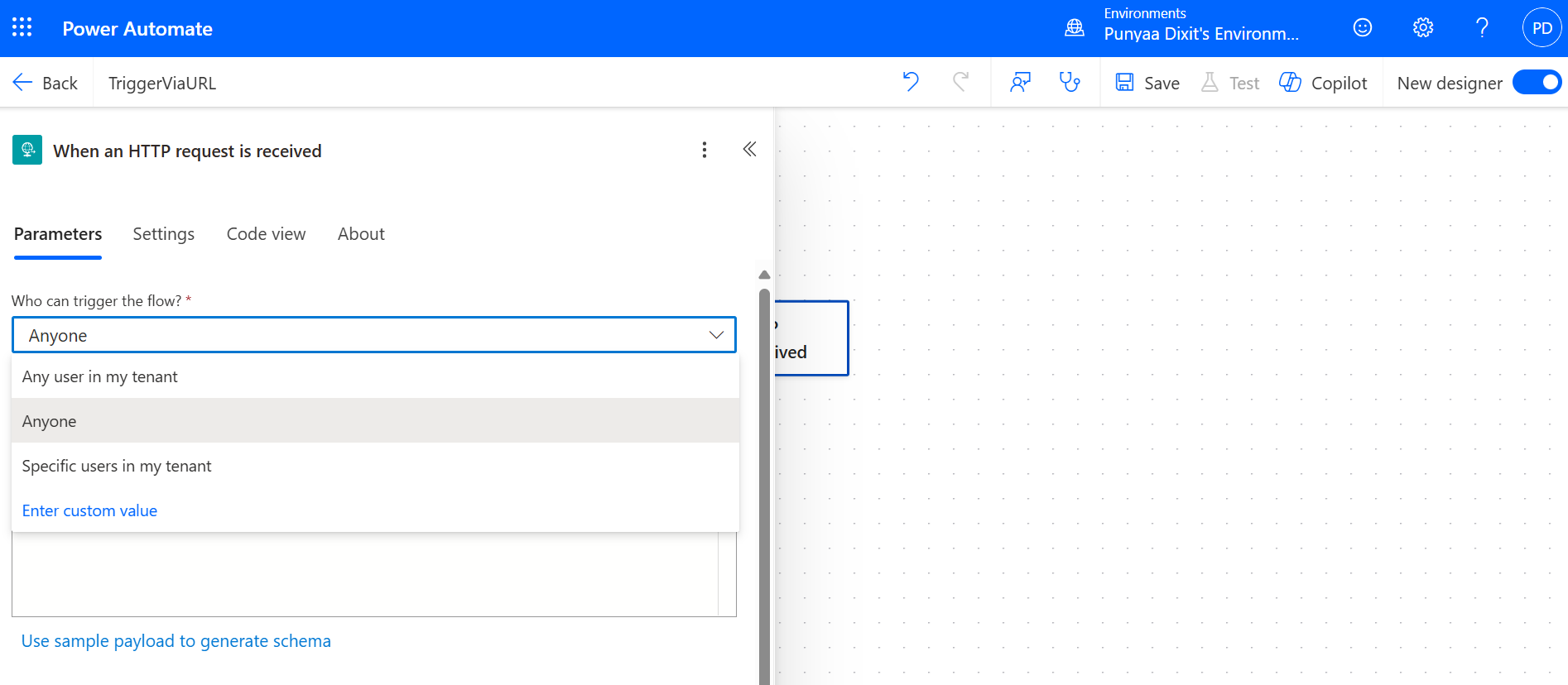
This allows your flow to receive structured data. For example, using the following payload schema:
{
“username”: “Mark.Holland”,
“action”: “start”
}
HTTP Methods – When to Use Which
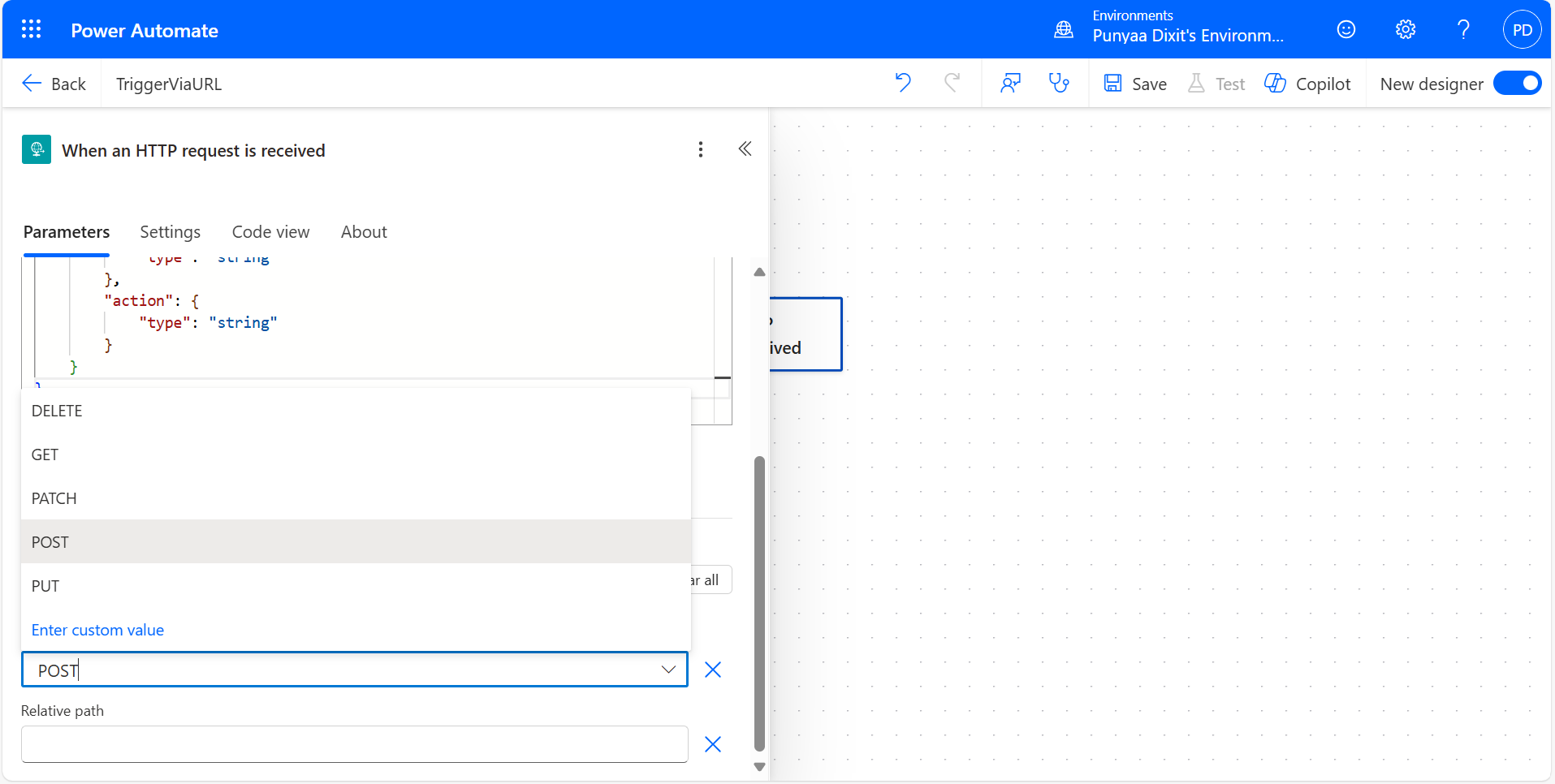
| Method | Purpose | When to Use |
|---|---|---|
| GET | Retrieve data (Read) | When you want to fetch or read information, no changes happen. |
| POST | Create or trigger actions (Write) | To trigger a flow, send data, or create something new. |
| PUT | Update or replace existing data | When you want to update an existing resource completely. |
| DELETE | Remove data | To delete a resource or request removal through an API. |
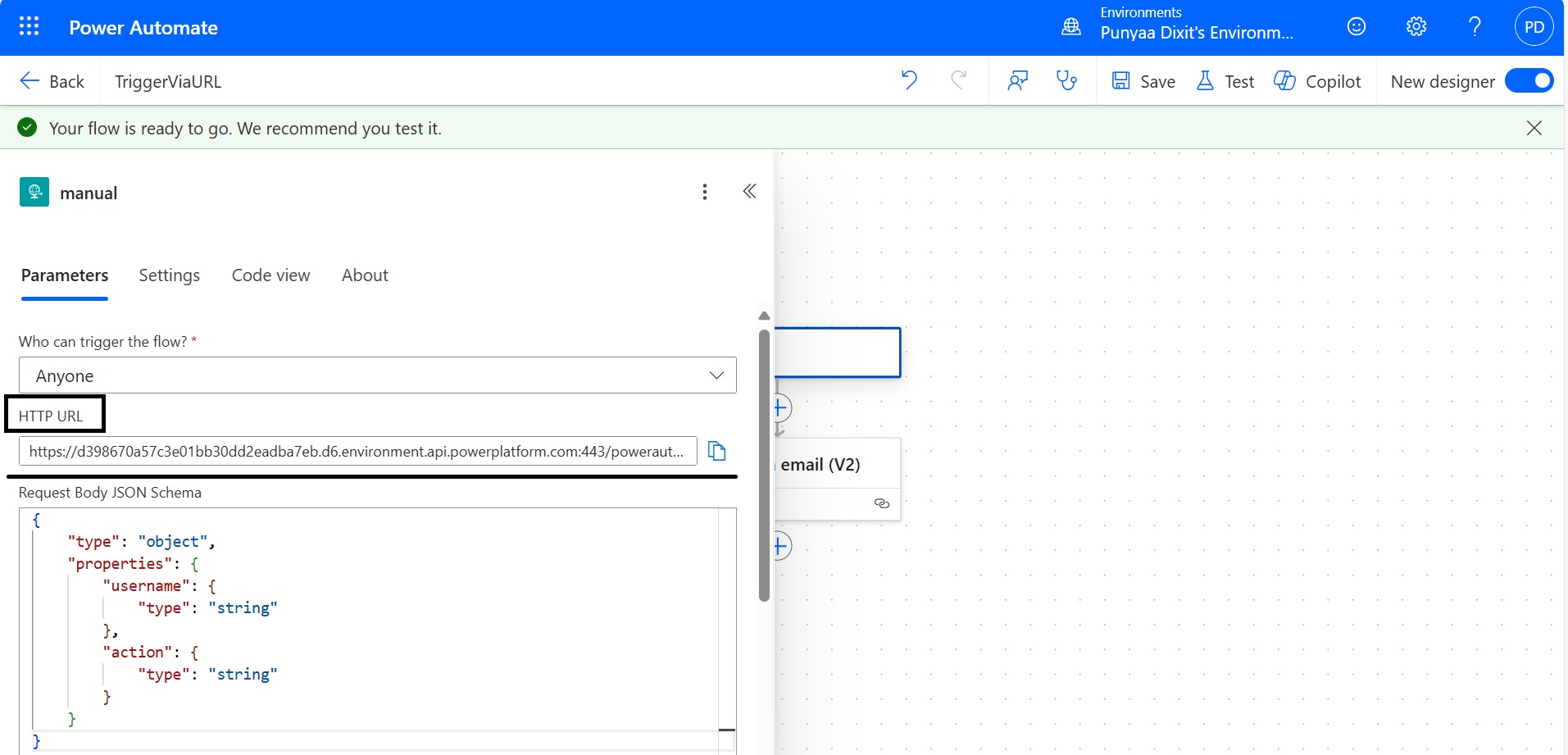
Step 3: Save and Get Your Power Automate Trigger URL
Once you have added at least one action (e.g., sending an email, updating a SharePoint list), save the flow. Power Automate will now generate a unique HTTP POST URL.
You can find it by clicking on the trigger again—it will look something like:
https://prod-00.westus.logic.azure.com:443/workflows/abc123/triggers/manual/paths/invoke?api-version=2016-10-01&sp=…
Step 4: Trigger the Flow
You can now trigger the flow using:
- Postman or curl for testing
- JavaScript fetch() from a web app
- PowerShell or Python scripts
- Other flows or systems that support HTTP POST
Let’s take the example of triggering the flow using a Python script. Here’s a simple code snippet:
As you can see, the flow was triggered successfully.
Use Cases
- Triggering workflows from external apps
- IoT devices sending data to Power Platform
- Custom buttons on intranet pages
- Webhook integrations with third-party services
Security Tips
- Avoid exposing the URL publicly—anyone with the link can trigger the flow.
- Use Azure API Management or Power Platform custom connectors for added security.
- Consider adding a shared secret or token validation in the flow logic.
Conclusion
Triggering Power Automate flows via URL is a simple yet powerful way to integrate automation into your apps, websites, scripts, or third-party systems. Whether you’re building custom buttons, integrating with IoT devices, or connecting external platforms, HTTP-triggered flows offer unmatched flexibility.
However, with this flexibility comes responsibility. Consistently implement proper security measures, validate incoming requests, and manage access carefully to protect your data and workflows.
By following the steps outlined in this guide and using the correct HTTP methods, you can confidently leverage Power Automate’s URL-triggering capabilities to streamline processes and build seamless, secure integrations.
Source: Read MoreÂ